[ad_1]
A menace group accountable for a sequence of malware-based espionage assaults in Singapore and Cambodia has been more and more concentrating on the Southeast Asian authorities sector to steal confidential knowledge, new analysis signifies.
The findings disclosed by cybersecurity agency Verify Level Analysis — present the operations have been carried out over a interval of seven months between December 2018 and June 2019, and leveraged spear phishing tips to lure victims into opening doubtful emails that downloaded malware on to their machines.
The hacking group — dubbed Rancor — enagaged in intelligent social engineering techniques by sending malicious paperwork from actual e-mail addresses belonging to authorities officers to make them appear extra legit. The targets have been authorities departments, embassies, and government-related entities in Southeast Asia, Verify Level mentioned.
Rancor was first documented by Palo Alto Networks’ menace intelligence group Unit 42 final July, who suspected the group of enagaging in cyber espionage assaults in opposition to Singapore and Cambodia utilizing spear phishing messages containing malicious attachments, resembling Microsoft Excel information with embedded macros and HTML functions.
A broad, persistent marketing campaign
Rancor’s methodology of using decoy paperwork — official letters, press releases, and surveys — to put in malware on victims’ machines hasn’t modified of their newest marketing campaign.
However the group has repeatedly mutated its techniques, methods, and procedures (TTPs) through the use of a variety of strategies, together with macros, JavaScript, recognized vulnerabilities in Microsoft Equation Editor, and even anti-virus packages with malicious libraries, to distribute malware.
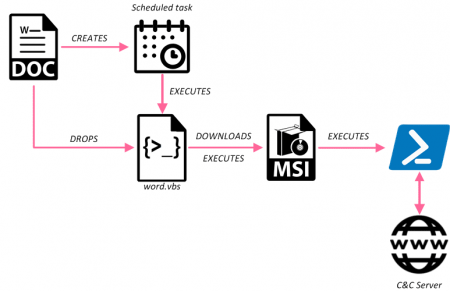
This ‘second stage payload’ then communicated with an attacker-controlled command-and-control (C&C) server to obtain the ‘last stage payload.’
In all, Verify Level noticed eight totally different waves of Rancor exercise in the course of the seven months. Tying all of them collectively have been overlapping indicators, resembling those talked about above and using ChangeIP.com for area decision.
Who’s behind it?
Verify Level researchers say using Equation Editor exploit (CVE-2018-0798) and the actual fact their C&C servers have been obtainable solely between 01:00 and 08:00 UTC time recommend a menace group of Chinese language origin.
Cybersecurity Agency Anomali Labs had reported earlier this July that a number of Chinese language menace actors have “up to date their weaponizer to use the Microsoft Equation Editor (EE) vulnerability CVE-2018-0798 late 2018.”
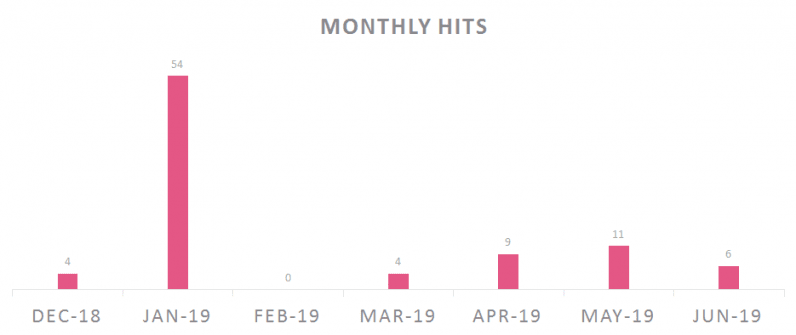
“Chinese language roots will also be confirmed by the presence of metadata in Chinese language for a number of the paperwork,” Verify Level acknowledged, including “the marketing campaign wasn’t lively throughout February 2019 which is a month of Chinese language New 12 months and Spring Pageant, an extended vacation in China.”
If something, the assaults spotlight the evolving methods of the cyberattack equipment assembled by Chinese language menace teams to allow large-scale surveillance not solely inside the nation, but in addition exterior it.
A report from Crowdstrike launched yesterday discovered state-sponsored hackers working for the Chinese language authorities deployed assaults in opposition to the biggest variety of trade verticals within the first half of 2019, together with telecom, gaming, well being care, manufacturing, and pharmaceutical sectors.
“We count on the group to proceed to evolve, continually altering their TTPs in the identical method as we noticed all through the marketing campaign, in addition to pushing their efforts to bypass safety merchandise and keep away from attribution,” the researchers concluded.
[ad_2]
Supply hyperlink
